Penetration Testing is the process of identifying security gaps in your IT infrastructure by simulating real world attacks. It works as a security assurance for your business systems.
Why Penetration Testing
Prevent Data Breaches
Detects and assessess the magnitude of the possible breach and helps improve the overall security response time to an attack.
Check Security Controls
Penetration testing ensures that the security system or controls in place are effective and mitigate the risks of an attack.
Discover Vulnerabilities
Having a penetration testing performed by cyber security experts enables you to identify security lapses, gaps, and weaknesses
Ensure Security of New Applications
Penetration testing determines threats and weaknesses in the applications and data to ensure security of critical IT infrastructure.
Meet Compliance Requirements
Network and application penetration testing can help ensure that your company is in complete compliance with the applicable security regulations as per the industry standards.
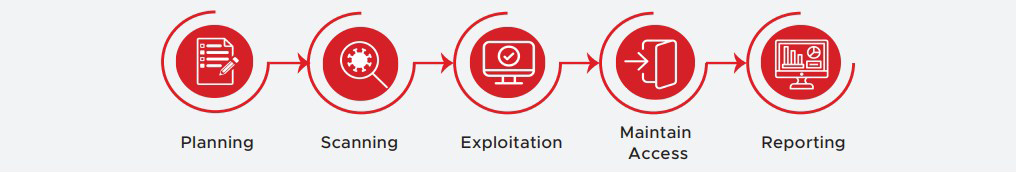
Penetration Testing Stages
Types of Penetration Tests
- Network Security
- Mobile & Web Applications
- System Security
- Database Security
- Cloud Security
Methods of Testing
Why Supersecure
We identify weaknesses the same way an attacker would, by hacking it. The unique Security Assessment methodology of Supersecure is based on best industry standards as we look to Discover, Exploit, Analyze and Report all the security holes that can be found in a system.
Our Penetration Testing services are designed to demonstrate how an attacker would gain unauthorized access to your environment by compromising in-scope systems and highlighting pivoting opportunities from compromised hosts.
Application Testing Services
Application penetration testing services have been designed to ensure that security weaknesses in your organization’s business critical applications are identified and fixed before malicious attackers and hackers exploit them. We have a dedicated team of application security experts who are trained, experienced and skilled to test the following platforms:
Web Applications
Web applications play a critical role for businesses to deliver services and information to the customers. As a result, conducting regular and timely penetration testing for web applications is an essential requirement for every business.
Supersecure’s security expertswould test your web applications by following the industry best-practices, such as OWASP Top 10, OSSTM, etc. They are armed with thelatest,most sophisticated skills and industry-leading experience. So you can be rest assured that Supersecure will help you root-out most vulnerabilities from your business-critical web applications.
Mobile Applications
As mobile applications are now being used to process the most sensitive data,it is essential to have them tested from the experts before launch or after any major or minorupdate.
Supersecure’s security experts are the first certified team of mobile applications security testing hence Supersecure iswell-positioned to deliver you the assurance of being tested by the best. Supersecure mobile application security testing techniques focus on ensuring that application security controls are acceptable, and the application logic does not allow unauthorized functionality. Supersecure has specialized experts to test mobile applications for all major platforms in-usetoday
Desktop & Legacy Applications
Desktop & Legacy Applications, mostly developed in-house, are always business critical and are often riddled with security flaws.
Supersecure desktop &legacy application testing helps organizations fully identify the vulnerabilities in their critical legacy applications. Through automated static assessments, manual reverse-engineering, and dynamic assessments, Supersecure’s security experts comprehensively assess legacy applications to deliver assurance to organizations.
Network Infrastructure Security Testing Services
Supersecure network infrastructure security testing services effectively identifies and validates weaknesses within an organization’s network infrastructure. Supersecure’s security experts use ‘best-in-class’ scanning tools and techniques to perform vulnerability assessments, assess network device configurations and identify network design flaws. Supersecure network infrastructure security testing services have been developed to ensure the following domains are effectively covered:
External/Internal Security Testing of Network Devices
Supersecure’s security experts employ a risk-based approach to effectively identify critical infrastructure vulnerabilities that exist on targeted internal systems and perform tests such as: VLAN hopping, MAC flooding, ARP spoofing and poisoning, stress testing, flooding packets, DOS attack with sustained TCP connectionetc.
Security Configuration Audit
Following best practices, such as the CIS benchmarks, Supersecure’s security experts conduct effective configuration audits of network devices to identify weaknesses and loopholes within their configurations. Thereby, delivering organizations the assurance that their network device configurations are hardened.
Database SecurityTesting
Database security is something that is often overlooked and taken for granted. Attackers take full advantage of this and target the critical business information stored in the database. This presents a tremendous challenge for security operations and management teams who need to ensure adequate security. Supersecure database security testing services are perfect for businesses that are concerned about the security of the information held within their database. We have a dedicated team of security experts who can provide anin-depth document edanalys is of whether the databases have been designed, configured and maintained securely. They can also verify compliance with the industry and vendor best practices. We offer awiderang eof services including database configuration audits, SOL injectiontests, in secures to ragee valuation, password policy evaluation and permissions evaluation.Subsequently,wealso provide a comprehensive report that provides security managers and compliance officers with ample information to make informed decision to improve the security of their existing databases.